Synopsis
The synopsis says to "follow" the rabbit you'll understand why...
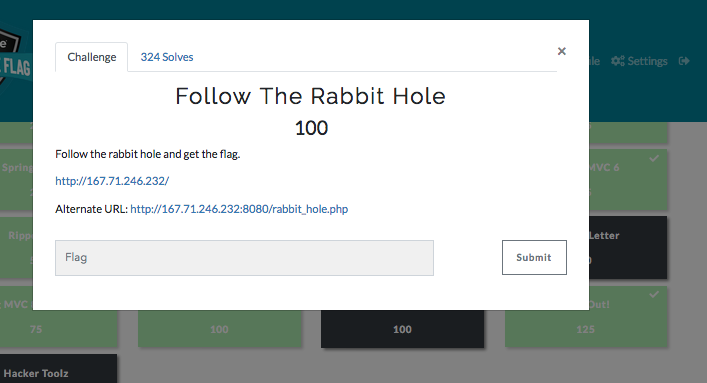
Step1: What to do ??
The web page shows us differents things...

But what to do next ? If we look closer, the get attribute "page" already has as parameter a base64 word, there is a kind of a same word in the web page. Let's try to replace it with the web page's word. Nice ! We have access to another web page
Step2: Let's follow the rabbit
Each web page conducts to another web page with the same kind of content. However, each one of them has a different first attribute. For example, the first page has: [513, '71'], the next one has [803, 'A5'] etc... At this point you need to guess that the first element of the attribute is a cell index and that the other one is the hex value of the cell. Let's retrieve them all in a big array.
Here is my script, I have just added a log file in case my idea was not the right one.
#!/usr/bin/env python3
import random
import string
import requests as rq
BASE="cE4g5bWZtYCuovEgYSO1"
def request_page(page):
url = "http://167.71.246.232:8080/rabbit_hole.php?page="
resp = rq.get(url+page)
return resp
def parse_resp(resp):
(num,new_page) =resp.split("\n");
(index,value) = num[1:-1].split(",")
return index,value,new_page[1:]
if __name__ == "__main__":
TAB = [""] * 2000 #A big Array to have enough space
page = BASE
f = open("Log_pages.log", "w")
while(1):
resp = request_page(page)
if len(resp.text) < 1:
break # Finish when there is no new cell in web page
(index,value,new) = parse_resp(resp.text)
TAB[int(index)] = value[2:-1] #Fill the tab
print("retrieve:" + "".join(TAB),end="\r")
page = new
f.write("[%s,%s]\n%s\n\n" % (index,value, page)) #Write logs
print("\n\nFinal TAB: " + "".join(TAB))
Here is what we retrieve
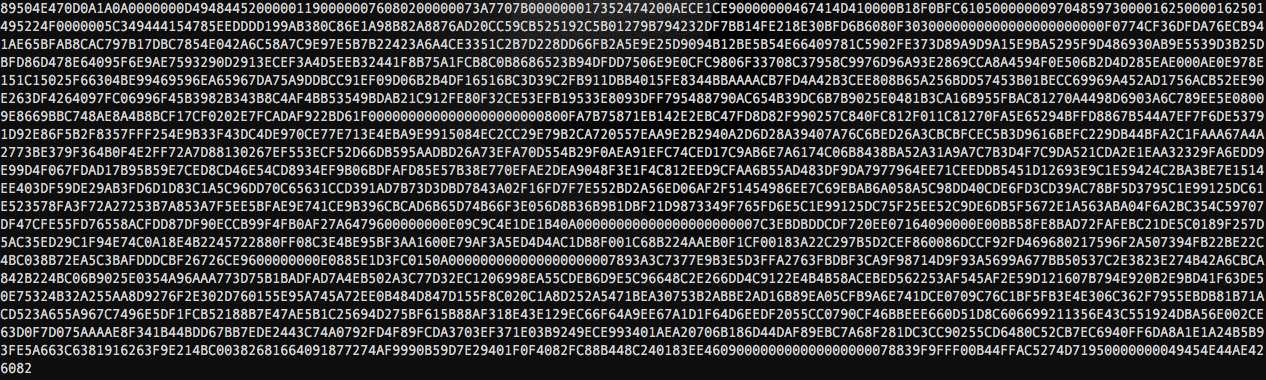
Step3: Flag it
The array look's like an hexdump of a file, we can try to decode it

Great ! this is a png file. And look at what was inside...

the flag: flag{automation_is_handy}
We are done, this was a really cool challenge.

Step1: What to do ??
The web page shows us differents things...

But what to do next ? If we look closer, the get attribute "page" already has as parameter a base64 word, there is a kind of a same word in the web page. Let's try to replace it with the web page's word. Nice ! We have access to another web page
Step2: Let's follow the rabbit
Each web page conducts to another web page with the same kind of content. However, each one of them has a different first attribute. For example, the first page has: [513, '71'], the next one has [803, 'A5'] etc... At this point you need to guess that the first element of the attribute is a cell index and that the other one is the hex value of the cell. Let's retrieve them all in a big array.
Here is my script, I have just added a log file in case my idea was not the right one.
#!/usr/bin/env python3
import random
import string
import requests as rq
BASE="cE4g5bWZtYCuovEgYSO1"
def request_page(page):
url = "http://167.71.246.232:8080/rabbit_hole.php?page="
resp = rq.get(url+page)
return resp
def parse_resp(resp):
(num,new_page) =resp.split("\n");
(index,value) = num[1:-1].split(",")
return index,value,new_page[1:]
if __name__ == "__main__":
TAB = [""] * 2000 #A big Array to have enough space
page = BASE
f = open("Log_pages.log", "w")
while(1):
resp = request_page(page)
if len(resp.text) < 1:
break # Finish when there is no new cell in web page
(index,value,new) = parse_resp(resp.text)
TAB[int(index)] = value[2:-1] #Fill the tab
print("retrieve:" + "".join(TAB),end="\r")
page = new
f.write("[%s,%s]\n%s\n\n" % (index,value, page)) #Write logs
print("\n\nFinal TAB: " + "".join(TAB))
Here is what we retrieve

Step3: Flag it
The array look's like an hexdump of a file, we can try to decode it

Great ! this is a png file. And look at what was inside...

the flag: flag{automation_is_handy}
We are done, this was a really cool challenge.
#!/usr/bin/env python3 import random import string import requests as rq BASE="cE4g5bWZtYCuovEgYSO1" def request_page(page): url = "http://167.71.246.232:8080/rabbit_hole.php?page=" resp = rq.get(url+page) return resp def parse_resp(resp): (num,new_page) =resp.split("\n"); (index,value) = num[1:-1].split(",") return index,value,new_page[1:] if __name__ == "__main__": TAB = [""] * 2000 #A big Array to have enough space page = BASE f = open("Log_pages.log", "w") while(1): resp = request_page(page) if len(resp.text) < 1: break # Finish when there is no new cell in web page (index,value,new) = parse_resp(resp.text) TAB[int(index)] = value[2:-1] #Fill the tab print("retrieve:" + "".join(TAB),end="\r") page = new f.write("[%s,%s]\n%s\n\n" % (index,value, page)) #Write logs print("\n\nFinal TAB: " + "".join(TAB))
Here is what we retrieve

Step3: Flag it
The array look's like an hexdump of a file, we can try to decode it

Great ! this is a png file. And look at what was inside...

the flag: flag{automation_is_handy}
We are done, this was a really cool challenge.

Step3: Flag it
The array look's like an hexdump of a file, we can try to decode it

Great ! this is a png file. And look at what was inside...

the flag: flag{automation_is_handy}
We are done, this was a really cool challenge.
The array look's like an hexdump of a file, we can try to decode it

Great ! this is a png file. And look at what was inside...

the flag: flag{automation_is_handy}
We are done, this was a really cool challenge.

Great ! this is a png file. And look at what was inside...

the flag: flag{automation_is_handy}
We are done, this was a really cool challenge.
